Tue, 18 Aug 2020 22:25:11
Staff ![]()
855
RakitAplikasi.com - The Onion Router or Tor is a network that allows users to remain anonymous on the internet and get rid of the possibility of surveillance, location tracking, etc. When using the internet. We can access the Tor network with the help of the modified Mozilla Firefox ESR web browser.
Tor allows someone to surf the web anonymously by masking the identity of the real user. It protects users from traffic analysis and network spying.
Tor is perhaps the most popular and secure option available for anonymous internet connectivity. To reduce confusion, we are talking here about the Tor network, not the web browser, which is used to access it.
Read More: New Linux Malware From Russian Hackers Is Stealing Data
History of Tor
Tor uses the principle of 'onion routing', developed by Paul Syverson, Michael G. Reed, and David Goldschlag at the United States Naval Research Laboratory in the 1990s. The alpha version of Tor, called 'The Onion Routing Project' or simply the TOR Project, was developed by Roger Dingledine and Nick Mathewson; was launched on September 20, 2002. Further development was carried out under the financial roof of the Electronic Frontier Foundation (EFF).
Tor Project Inc. is a non-profit organization that currently manages Tor and is responsible for developing it. It has received funding mainly from the US government, and additional assistance from the Swedish Government and various NGOs & individual sponsors.
How Tor Works?
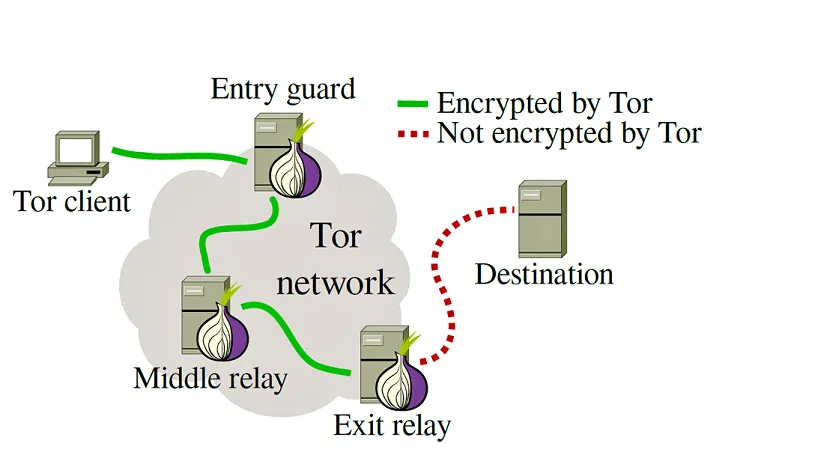
The answer to how to work is quite simple. Tor uses the concept of the 'onion routing' method where user data is first encrypted and then transferred through different relays on the Tor network. In doing so, it creates multi-layered encryption (a layer like an onion) and keeps the user's identity safe.
One layer of encryption is decrypted in each successive Tor relay, and the remaining data is passed to any random relay until it reaches its destination server. For the destination server, the last Tor node/relay exit appears as the data origin. Therefore, it is difficult to trace the identity of a user or server with any surveillance system acting as an intermediary.
Apart from providing anonymity to independent users, Tor can also provide anonymity to websites and servers in the form of Tor Hidden Services. Also, P2P applications like BitTorrent can be configured to use the Tor network and download torrent files.
Controversy and Influence
People often praise Tor for the anonymity and privacy it provides to users who want to bypass censorship, who are harassed and traumatized by stalkers, and social activists who fear being caught by the authorities. Sometimes, it is also used by different security agencies to share confidential information.
NSA rapporteur Edward Snowden uses Tor to leak information about PRISM to The Guardian and The Washington Post.
However, the stories are not all that great. Tor has faced criticism for acting as a medium for various illegal activities such as data breaches, drug trafficking, gambling, and hosting dark websites. Tor is also used by criminal minds to communicate over the internet while hiding their identities, which makes it difficult for security agencies to track them down.
The US National Security Agency (NSA) calls Tor "the king of Internet anonymity with high security and low latency". Dan has received similar comments from BusinessWeek magazine, "perhaps the most effective way to beat the online surveillance efforts of intelligence services around the world."
Another speculation made is that Tor took its funding from the U.S. Government, which could lead to the assumption that the NSA may have compromised the identity of individual Tor users. However, former Tor executive director Andrew Lewman denies any confederation with the NSA.
Is Tor Safe?
Various claims have been made about compromising Tor's anonymity and security over time. The most famous is the Bad Apple Attack, in which researchers claim to have identified around 10k IP addresses of active BitTorrent users connected via Tor.
The Heartbleed bug was behind another major compromise in April 2014, which shut down the Tor network for several days.
Traffic Fingerprinting is a method used to analyze web traffic by analyzing patterns, responses, and packets in a specific direction. This technique can be used to attack the Tor network by making the attacker's computer act as a guard.
The major vulnerabilities are found at egress points, where the level of security is very low compared to other Tor networks.
What is Tor Browser?
Tor Project Inc. has released Tor Browser, which is a modified version of the Extended Support Release (ESR) version of the Mozilla Firefox browser. The browser is portable so it can be used from external media and also reduces installation hazards.
Tor Browser deletes browsing history and cookies after each use, reducing the risk of cookie tracking. We can configure a SOCKS (Socket Secure) based application to use the Tor network by configuring it with a loop-back address.
It is also known as a dark web browser as it allows users to browse what is called dark websites which can be accessed on the normal web.
The Tor browser is available for a variety of desktop operating systems, including Windows, Linux, and macOS. You can visit this link to download the latest version of Tor Browser for Windows, Linux, and macOS.
Read More: New Mac Ransomware Spreads Through Pirated Software
How to download the Tor browser?
How to install Tor Browser on Windows 10/7/8?
- Run the Tor Browser setup.
- Choose your desired language.
- On the next window, choose the destination folder. Using Tor would be easy if you choose the Desktop as the destination.
- Click Install.
Tor Settings will create a folder called Tor Browser on your Desktop. Open the folder, and run the shortcut file to use the Tor Browser.
For Linux, you'll need to extract the downloaded files, using either the command line or a file extractor app.
Tor Browser for Android
Tor Browser - the official Tor app for Android
Orbot - a free proxy app by Tor for Android devices.
Orfox - the mobile version of the Tor Browser for Android devices. (Terminated)
The Guardian Project, a global community of developers founded by Nathan Freitas, will be credited for developing Orfox.
Tor Browser for iOS
The Tor browser app for iOS created by Tor Project core contributor, Mike Tigas.
Tor Alternatives
I2P and Freenet are other anonymity networks that can act as alternatives to Tor. Additionally, Tails and Subgraph OS are Linux-based distributions with built-in Tor support. In the past, Hornet was also an anonymity network providing higher network speeds compared to Tor.
Should I Use Tor?
Tor has proven to be an excellent medium for a secure, protected, and anonymous web presence available to users free of charge. Tor's developers don't intend to turn Tor into a hotbed of illegal activity, but evil-minded people have used Tor to their advantage such as selling illegal items on dark websites. The Tor project has produced an optimistic approach to censorship and a surveillance-free Internet.
You can use Tor if you want to hide your identity on the web or access some websites that are blocked in your area. However, stop yourself from doing anything illegal because nothing has proven unreasonable, and they can still arrest you. Additionally, accessing your social media accounts through Tor can reveal your identity.
For more ideas on 'How Tor works,' check out the video:
Keywords: what is tor browser, how tor browser works, tor browser, tor browser for android, tor browser for ios, tor browser download
Also Read: